Authenticating Your Git Client for Private Repositories
To push or pull from a private repository, your Git client must be authenticated.
While authentication is generally straightforward, the exact steps depend on the Git client you’re using.
OAuth HTTPS – Automatic Web Login
For Git clients like Git Bash CLI or tools integrated into platforms like Altium Designer, authentication is handled via OAuth HTTPS using your web browser.
How It Works:
When you attempt to push or pull from a private repository, the Git client will automatically prompt you to open your web browser.
The browser will direct you to a login page where you can grant the necessary permissions.
Note: You may need to log in to hub.allspice.io before you can authorize the connection.
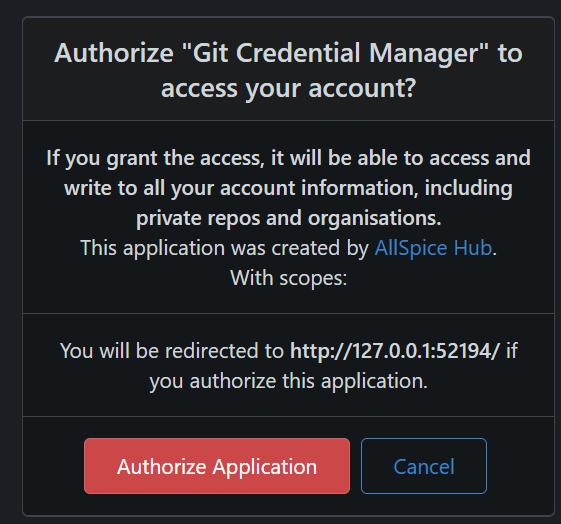
Once authorization is complete, you should be able to push and pull without issue.
If your client requests a username/password, you may need to switch from Windows Credential Manager to Git Credential Manger
📂 Changing Git Credential Manager
Overview
For improved compatibility with modern Git services and faster onboarding, we recommend switching to Git Credential Manager (GCM) for managing Git authentication.
- Git Credential Manager supports:
- OAuth-based authentication.
- Single Sign-On (SSO) workflows.
- Multi-Factor Authentication (MFA).
- Modern Git hosting platforms like GitHub, GitLab, Bitbucket, and Azure DevOps.
This change simplifies credential storage and supports enhanced security workflows.
How to Switch to Git Credential Manager
Run the following command in your terminal:
git config --global credential.helper manager
This tells Git to use Git Credential Manager (GCM) as the system-wide credential helper.
🔧 Note:
manager-core is the latest version of Git Credential Manager, fully supported on modern Git clients.
What This Changes
✅ Git will start using Git Credential Manager to store and retrieve credentials.
✅ GitHub, GitLab, Bitbucket, and other modern services will authenticate using OAuth or Personal Access Tokens (PATs).
✅ All future Git authentication prompts will be handled by Git Credential Manager.
⚠️ Important Warnings & Caveats
1. Scope of Change
This change affects all Git operations on this machine.
If you use Git for multiple services (GitHub, GitLab, internal Git servers, CI/CD scripts), those workflows will now route through Git Credential Manager.
2. Legacy Credentials Become Unused
Any Git credentials previously stored in the Windows Credential Manager will no longer be accessed by Git.
These credentials remain in the system but will not be used unless you manually switch back.
3. Automation and CI/CD May Break
Non-interactive scripts, batch jobs, and CI pipelines that previously used Windows Credential Manager for cached Git credentials may fail until updated to support the Git Credential Manager authentication flow.
You may need to reconfigure CI/CD environments to use Personal Access Tokens or device authentication flows supported by GCM.
4. Internal Git Servers May Require Special Handling
If you use internal Git servers that rely on basic username/password authentication and do not support OAuth or token-based authentication:
Git Credential Manager may not be compatible.
Consider using SSH-based authentication for those services.
Validate internal Git compatibility before switching.
5. Git Client Compatibility
Git Credential Manager is supported in Git versions 2.29 and later.
Older Git clients may not work correctly with GCM.
💡 Troubleshooting & Rollback
If you encounter issues:
You can revert to using the Windows Credential Manager by running:
git config --global --unset credential.helper
git config --global credential.helper wincred
For SSH-based workflows, this change has no impact.
If you need help resolving credential issues, please contact your system administrator or support team.
📌 Summary
| Feature | Git Credential Manager | Windows Credential Manager |
|---|---|---|
| Scope | Git-only | System-wide (multi-app) |
| Storage | GCM store | OS-level credential vault |
| Authentication | OAuth, SSO, MFA, PATs | Username/Password |
| CI/CD Compatibility | Requires token setup | May rely on cached credentials |
| Multi-Git Server Support | Supports modern services | Supports older/legacy systems |
Authentication by PAT
Username and Password or Personal Access Token (PAT)
For many Git clients, like GitHub Desktop, you can authenticate using a username and password or a Personal Access Token (PAT).
If you would like to keep using the Windows Credential Manager, you can log in using your credentials for hub.allspice.io.
Alternatively, you can generate a PAT and authenticate using your username/email and the generated token.
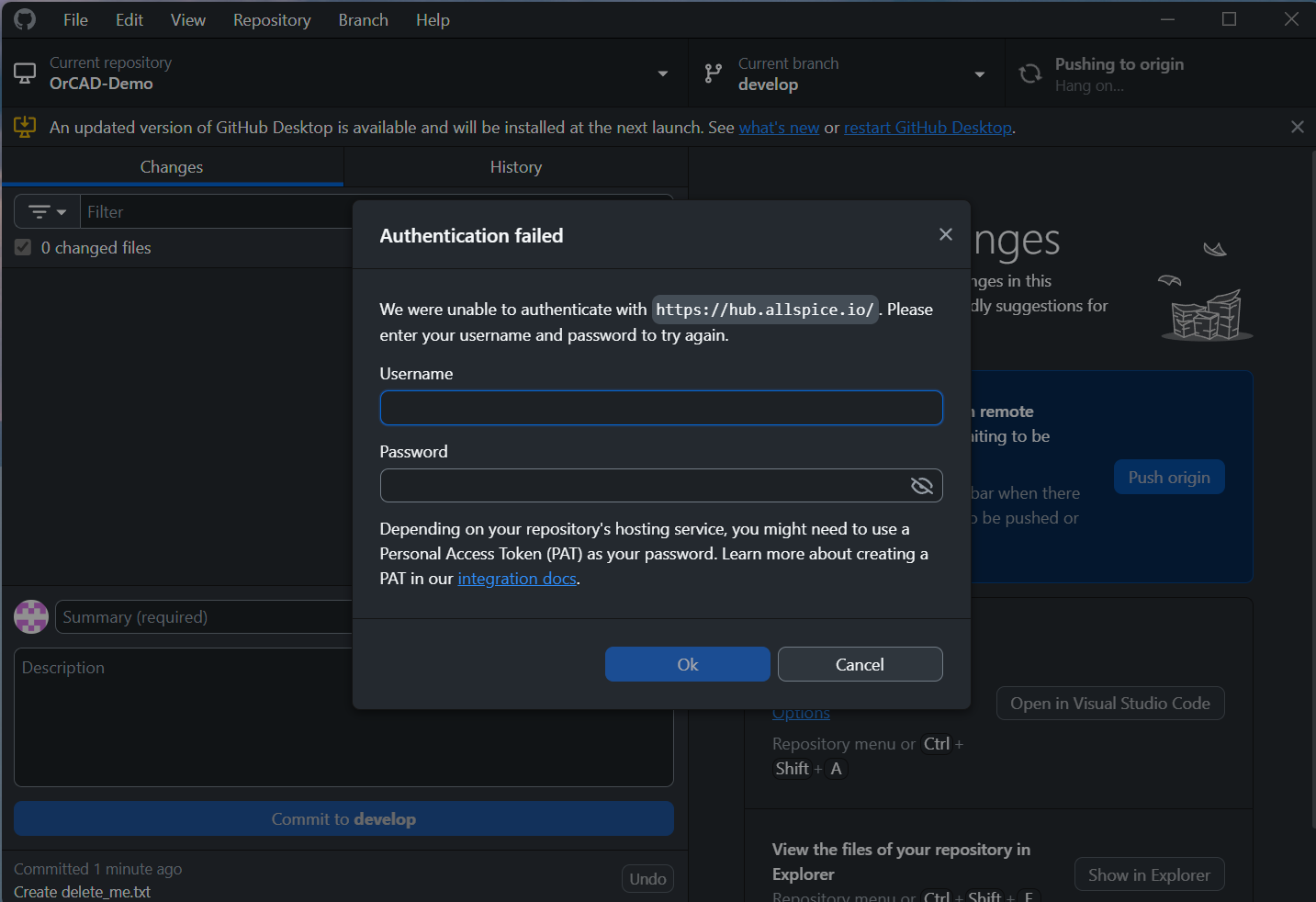
Troubleshooting Authentication Issues
Authentication can sometimes be tricky due to variations across Git clients and credential managers.
Recommended Steps:
Capture Screenshots: If you encounter issues, take screenshots of the login prompts or error messages.
Contact Support:
Email the screenshots and a brief description of your issue to support@allspice.io. We’re happy to assist and can schedule a call to walk you through complex situations.
Be Cautious with Credentials: Avoid deleting or modifying stored credentials unless instructed. Incorrect changes can disrupt your workflow.